A Platform App can be set up to use client-side OAuth 2.0 authentication.
Learn how OAuth 2.0 authentication works
Prerequisites
To set up a Platform App using OAuth 2.0 authentication, you will need to ensure
you have access the Developer Console from your Box enterprise
account. Alternatively, you may sign up for a developer account.
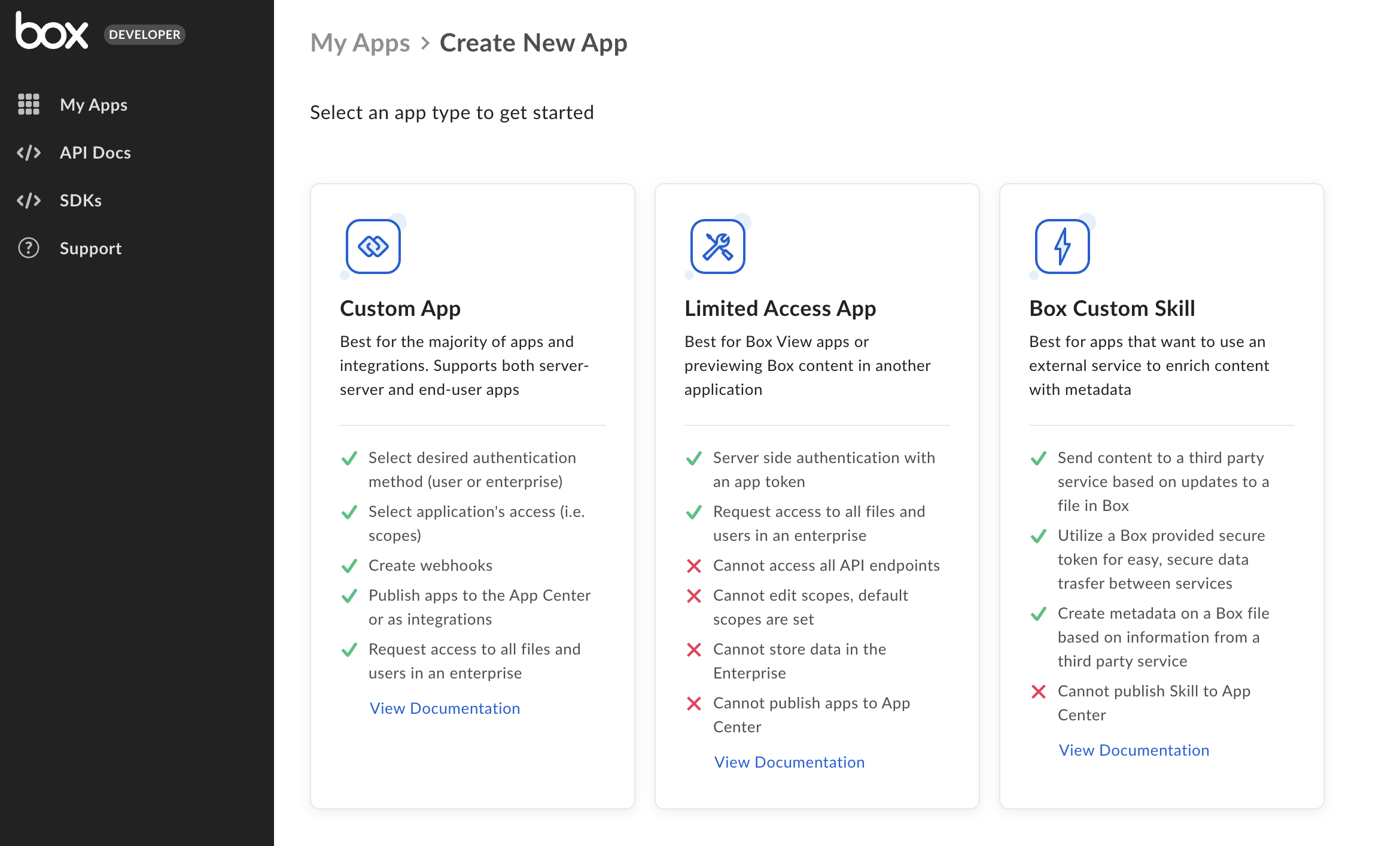
App creation steps
Navigate to the Developer Console
Log into Box and go to the
Developer Console. Select Create Platform App.
Select application type
Select Platform App from the list of application types. A modal will appear to
prompt a selection for the next step.
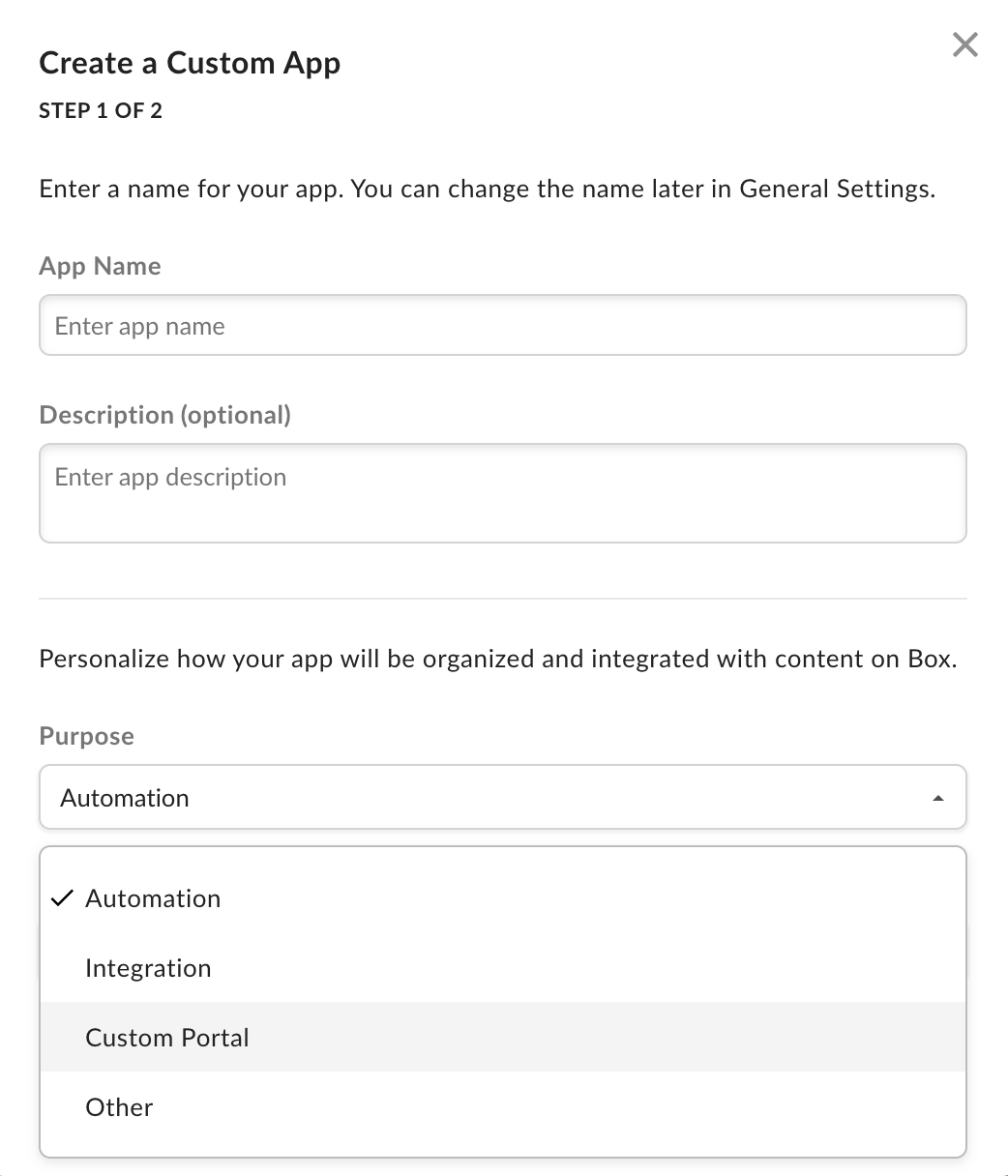
To describe your app, provide an app name and description.
Use the drop-down list to select the app’s purpose. Depending on the option chosen, you might need to specify further details.
| Purpose | Details |
|---|
| Automation, Custom Portal | Specify if the app is built by a customer or partner. |
| Integration | Specify the integration category, external system name if the app is built by a customer or partner. |
| Other | Specify the app purpose and if it is built by a customer or partner. |
Select application authentication
Select User Authentication (OAuth 2.0) and confirm with Create App.
Once you make a selection, you will not be able to change to a different
authentication method without creating a new application.
Basic configuration
Before the application can be used, some additional configuration is
required.
Redirect URI
During the OAuth 2.0 flow, users are redirected to their browser to
authenticate and then authorize the application to take actions on their behalf.
Prior to redirecting the user, Box verifies that the redirect_uri parameter
passed into the authorization URL matches one of the redirect
URIs configured for the application. This will be an exact match check, meaning
the URIs must be exactly the same. Localhost and loopback address redirect URIs
will be permitted redirect to any port, but the scheme, domain, path and query
parameters must match one of the configured URIs.
You can configure these under the OAuth 2.0 Redirect URI section on the
Configuration page in the developer console. These must be valid URIs that are
HTTPS, or a less secure HTTP for localhost or loopback address. We do not
permit duplicate URIs to be saved.
Starting November 29, 2021, new applications using OAuth 2.0 will
require the URIs set in the configuration tab of the Developer Console to
strictly match the one used during redirect. In addition, both new and
existing applications, will gain the ability to add multiple redirect URIs.If you configured multiple redirect URIs for the application,
the authorization URL must include the redirect_uri parameter matching one
of the URIs configured in the developer console.
If the parameter is not specified, the user will see a redirect_uri_missing
error and will not be redirected back to the app after granting application
access.For existing applications, the deadline to make changes to this URL to avoid
service disruption is May 13, 2022.
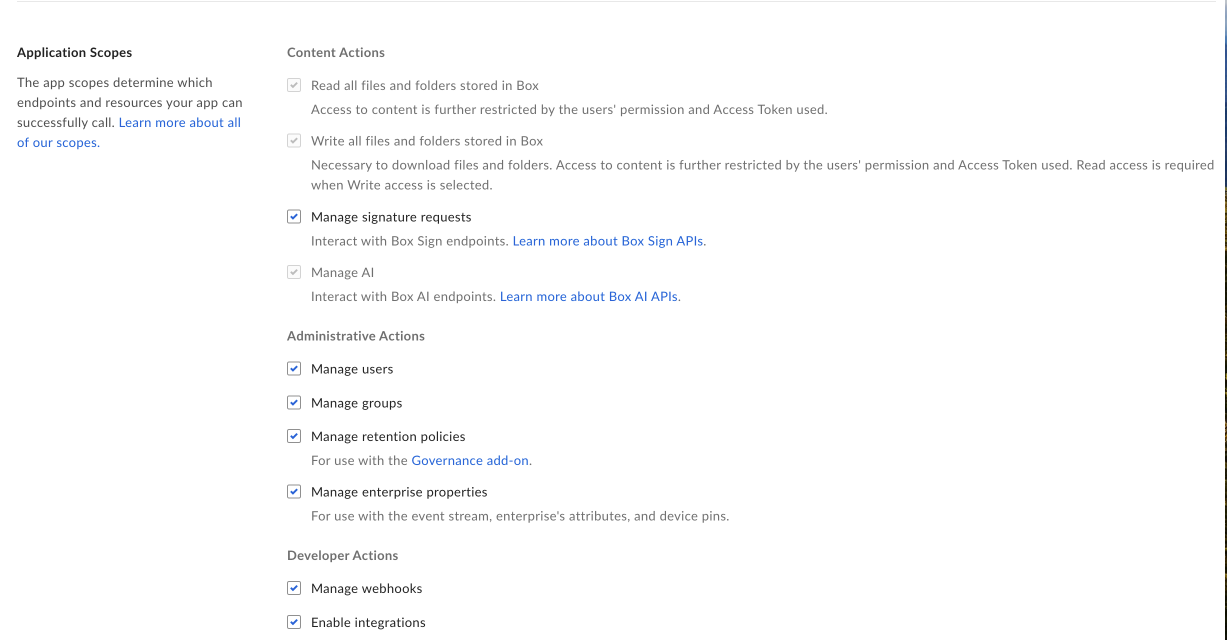
Application Scopes
Scopes define what permissions your application has in order to access data. See
the scopes guide for detailed information on each option.
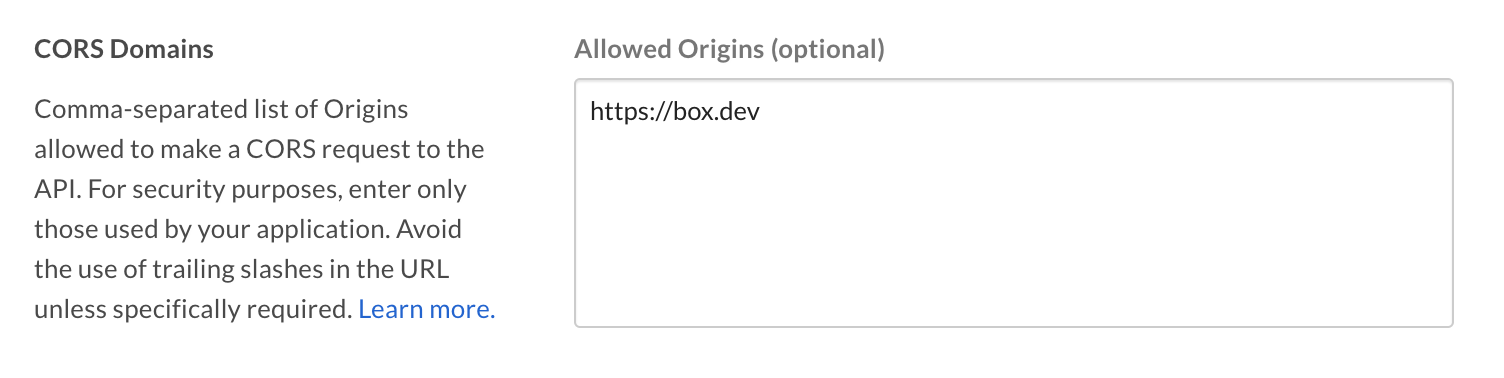
CORS Domains
If your application makes API calls from front-end browser code in
Javascript, the domain that these calls are made from will need to be
added to an allow-list due to Cross Origin Resource Sharing,
also known as CORS. If all requests will be made from server-side code,
you may skip this section.
To add the full URI(s) to the allow-list, navigate to the CORS Domain
section at the bottom of the Configuration tab in the
Developer Console.