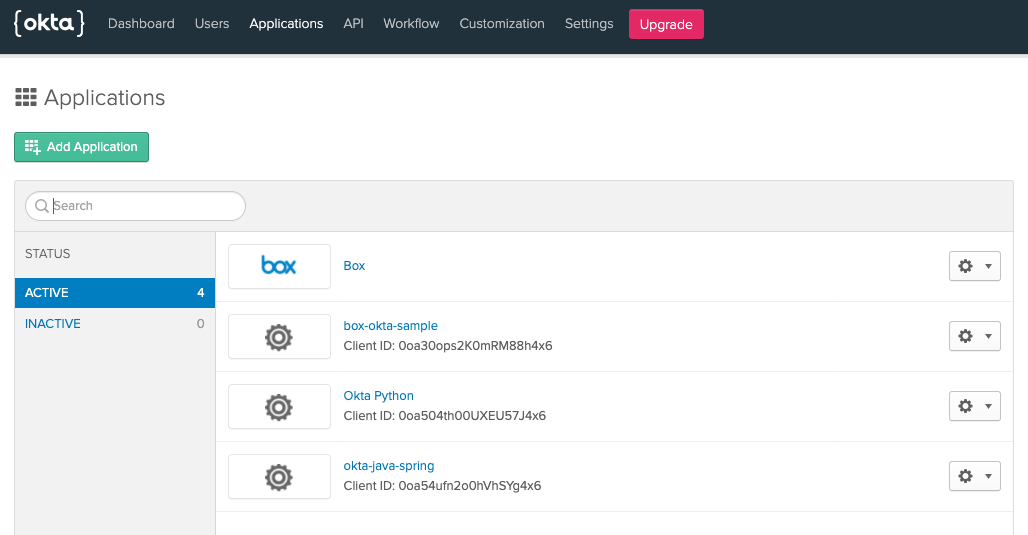
Create an Okta Application
Starting from the Okta developer site, sign up for a new developer account, or log in under your personal account if you already have one. If you’re logging in with an existing account, you should see the Okta dashboard. Click on the Admin button at the top right.
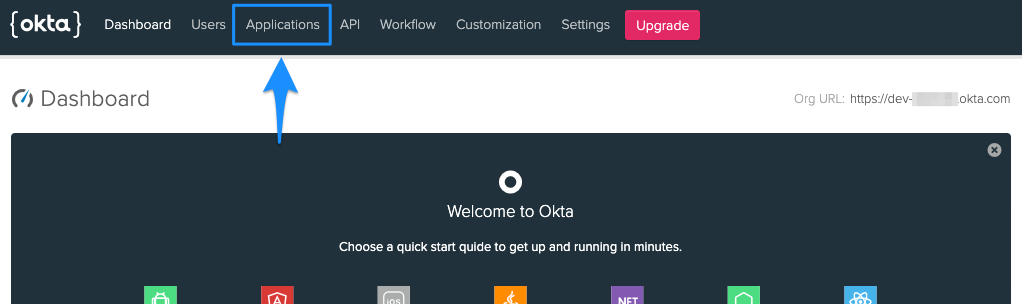
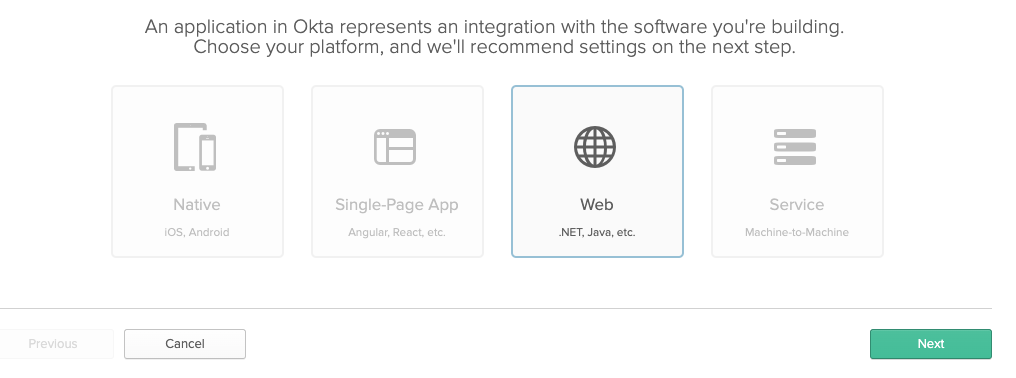
Copy Application Credentials
Using the configuration files set up in the last step, we next have to add in the Okta application org and app details within the files. Most Okta application information can be found on the general settings page, with the exception of theOrg URL that is used in the configuration URIs to
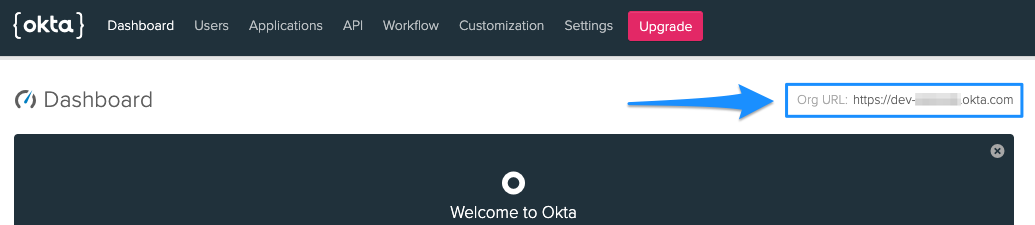
reference back to your Okta organization. To obtain the Org URL, go to the
dashboard of your Okta admin console. The Org URL will be in the top right
corner of the screen.
Depending on the language and framework previously chosen, we’ll set up the
appropriate configuration files.
Create a User
Our last step in the Okta setup is to create a test user that we will use to log in to the application.- Go to the Users section of the Okta admin dashboard.
- Click on the Add Person button.
- Enter all appropriate user info. Under password, select Set by admin and input a password for the user. Also deselect the User must change password on first login option. You will use the username and password to log in. These settings will only be used for testing purposes and are not best practices for user creation and security.
- Click the Save button to create the user.
Summary
- You created an Okta application.
- You updated the Okta configuration information in the local application.
- You created a test Okta user.
